Blake2s256 message digest algorithm ; Hi sbernard, Apologies for the time to get back to you Could you help me to understand the full scope of your project, end goal, why is scandium server necessary etc Kotlin // Although you can define your own key generation parameter specification, it's // recommended that you use the value specified here val keyGenParameterSpec = MasterKeysAES256_GCM_SPEC val mainKeyAlias = MasterKeysgetOrCreate(keyGenParameterSpec) // Create a file with this name, or replace an

Zabbix4 X How Secure Data Secure Data Programmer All
Tls_rsa_with_aes_128_cbc_sha256
Tls_rsa_with_aes_128_cbc_sha256-Since this is only the minimum version, if, forexample, TLSv10 is negotiated then both TLSv10 and SSLv30 ciphersuites are availableNote these cipher strings do not change the negotiated version of SSL or TLS, they only affect the listof available cipher suitesAES128, AES256, AEScipher suites using 128 bit AES, 256 bit AES or either 128 or 256 bit AESAESGCMAES in Galois Counter ModeMatrixSSL is an opensource TLS/SSL implementation designed for custom applications in embedded hardware environments The MatrixSSL library contains a full cryptographic software module that includes industrystandard public key and symmetric key algorithms It is now called the Inside Secure TLS Toolkit



How To Solve Problem Active Check Update From Started To Fail Ssl Write Timed Out Zabbix Forums
To enable SSL connections you need to Update mysql_servers use_ssl for the server you want to use SSL;The Rambus TLS Toolkit (formerly known as MatrixSSL from Inside Secure) is a TLS protocol implementation in C language with minimalistic system dependencies, making it easily portable on any platform, ranging from embedded devices with lightweight capabilities toRFC 5487 TLS PSK New MAC and AESGCM March 09 o ECCbased cipher suites with SH56/384 and AESGCM in The reader is expected to become familiar with these two memos prior to studying this document 11Applicability Statement The cipher suites defined in Section 3 can be negotiated, whatever the negotiated TLS version is The cipher suites defined in Section 2 can be
Weak DHERSADESCBC3SHA Recommended DHEDSSAES128GCMSH56 Weak PSKCHACH0POLY1305 Insecure ADHAES256SH56 Weak ECDHEECDSAAES128SH56 Weak ECDHEECDSACAMELLI56SHA384 Weak SRPAES256CBCSHA Insecure ECDHEPSKNULLSHA Weak PSKAES128CCM8I'm skipping everything not related to the Cipher Suites, and a lot of detail even there, but I'll get into it a bit more#listenersslexternalciphers = ECDHEECDSAAES256GCMSHA384, listenersslexternalpsk_ciphers = PSKAES128CBCSHA,PSKAES256CBCSHA,PSK3DESEDECBCSHA,PSKRC4SHA 1 2 3 Then enable the emqx_psk_file plugin $ emqx_ctl plugins load emqx_psk_file 1 The configuration file for PSK is etc/psktxt A colon is used to separate
Hashes blake2b512 message digest algorithm;This document describes a set of preshared key cipher suites for TLS that uses stronger digest algorithms (ie, SH56 or SHA384) and another set that uses the Advanced Encryption Standard (AES) in Galois Counter Mode (GCM) Badra Standards Track Page 1 RFC 5487 TLS PSK New MAC and AESGCM March 09 Table of Contents 1The last part is the encryption algorithm, AES 128 bit with GCM It is important to note that if you can often connect to services with Chrome when other applications fail This is because Chrome implements its own version of the Cipher suites, so it is not dependent on what the OS is capable of



How To Solve Problem Active Check Update From Started To Fail Ssl Write Timed Out Zabbix Forums
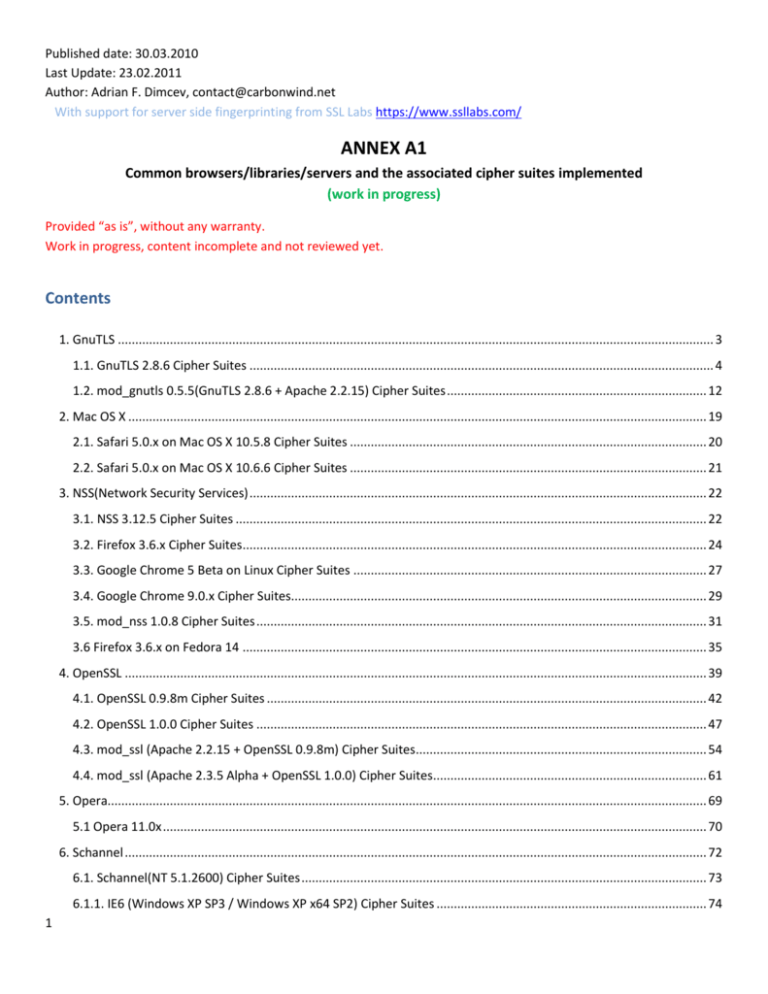



Table 4 1 Experimental Cipher Suites
HAProxy implements this part of security with the following lines ssldefaultbindciphers ssldefaultserverciphers And Nginx implements the same thing with ssl_ciphers ; Issue/Introduction Learn which TLS ciphers, hashes, and cipher suites are supported by Symanteccloud services such as Email Encryptioncloud and Email Securitycloud at the day of publication of this articleOpenssl on RHEL6 is originally based on openssl100 but was rebased to openssl101e with RHEL65 This article is part of the Securing Applications Collection Due to the serious flaws uncovered in openssl during the lifetime of RHEL6 you should always use




Linux Octopus Tentacle Not Installing Octopus Server Octopus Deploy



Openssl Iana Tls Cipher Suites What Would Jeremy Combs Do
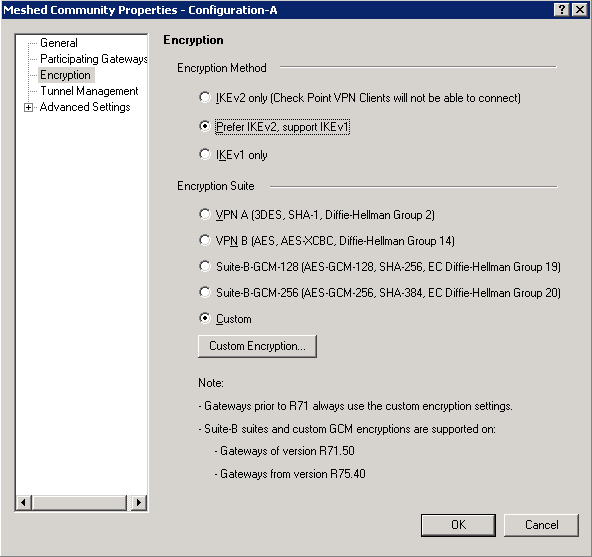
To add cipher suites, either deploy a group policy or use the TLS cmdlets To use group policy, configure SSL Cipher Suite Order under Computer Configuration > Administrative Templates > Network > SSL Configuration Settings with the priority list for all cipher suites you want enabled To use PowerShell, see TLS cmdletsGost message digest algorithm; Cipher suite correspondence table IANA, OpenSSL and GnuTLS use different naming for the same ciphers The table below lists each cipher as well as its corresponding Mozilla Server Side TLS compatibility level Hex Priority IANA GnuTLS NSS OpenSSL



Build The Gat At Xin At




Elb Insecure Ssl Ciphers Trend Micro
Disable weak cipher suits with Windows server 16 DCs We have disabled below protocols with all DCs & enabled only TLS 12 SSL v2, SSL v3, TLS v10, TLS v11 We found with SSL Labs documentation & from 3rd parties asking to disable below weak Ciphers As of now with all DCs we have disabled RC4 128/128, RC4 40/128, RC4 56/128, RC4 64/128 # openssl ciphers v 'high!sslv2!adh!dhe!dh!3des!md5!anull!enull!null@strength' ecdhersaaes256gcmsha384 tlsv12 kx=ecdh au=rsa enc=aesgcm(256) mac=aead ecdheecdsaaes256gcmsha384 tlsv12 kx=ecdh au=ecdsa enc=aesgcm(256) mac=aead ecdhersaaes256sha384 tlsv12 kx=ecdh au=rsa enc=aes(256) mac=sha384 ecdheecdsaaes256 I am using a MEMCM Task Sequence to build servers running Windows Server 19 So far, I build 22 servers with this OS At the end of OSD, on of



Cisco Com



Applied Crypto Hardening Bettercrypto Org
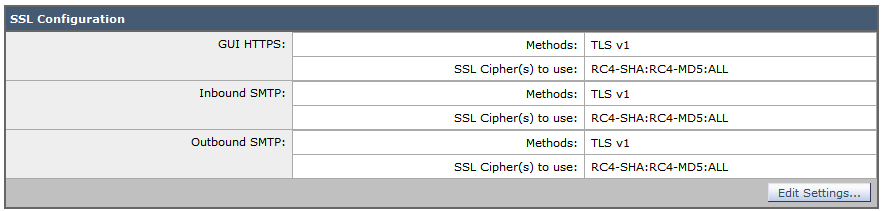
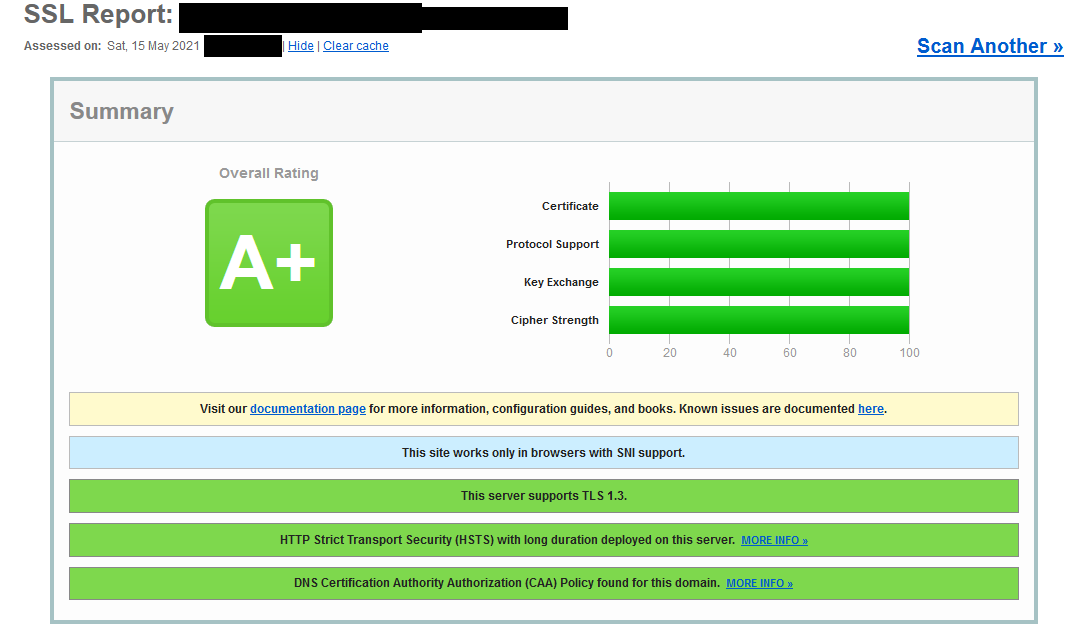
OpenSSL considers this as a valid string If AES128_SHA is configured instead of AES128SHA (using an underscore instead of a hyphen) however, OpenSSL identifies this as an invalid cipher suite Authenticated Mode (NULL Ciphers)About Cipher Suites Cipher Suites are groups of cryptographic algorithms used in a TLS connection Clients send a list of cipher suites they support in the Client Hello, and the server selects one and responds with it in the Server Hello This table lists the relative support of cipher suites by clients and servers Cipher SuiteIn last year general plan Announcing SSL Labs Grading Changes for 17 there is a statement if server uses only Forward Secrecy ciphers the grade will go down to B This hasn't happened yet, but currently implemented ssllabs test there is a warning that servers only supporting nonforward secrecy ciphers grade will be reduced to B from March 18




날으는물고기 Security Server Side Tls Recommended Configurations



Applied Crypto Hardening Bettercrypto Org
By default only TLSv12 is supported as older versions have known security weaknesses allowing 3 rd parties to impersonate your device and potentially access and compromise transmitted data To support legacy hardware, such legacy versions can be enabled per IoTConnector while device maker is made fully awareIt can consist of a single cipher suite such as RC4SHA It can represent a list of cipher suites containing a certain algorithm, or cipher suites of a certain type For example SHA1 represents all ciphers suites using the digest algorithm SHA1 and SSLv3 represents all SSL v3 algorithms Lists of cipher suites can be combined in a single Apache SSL Cipher Suites Perfect Forward Secrecy I was interested to tune my https sites with Apache to support only cipher suites that use the ephemeral DiffieHellman key exchange = perfect forward secrecy But after searching a while through the Internet, only SSLCipherSuite with a few concrete algorithms were presented, while I wanted to



How To Disable Sslv3 With Haproxy Netgate Forum




Elb Insecure Ssl Ciphers Trend Micro
SRPRSAAES128CBCSHA SRPAES128CBCSHA RSAPSKAES128CBCSHA PSKAES128CBCSHA schoen , 326am #17 rg305 SH then SHA1 then 3DES then RC4 then MD5 (as needed) This doesn't really make sense These things are not comparable (SHA and MD5 are hash functions, while 3DES and RC4Supported SSL / TLS ciphersuites The following key exchanges and ciphersuites are supported in mbed TLS mbed TLS uses the official NIST names for the ciphersuites For reference purposes, the OpenSSL equivalent of the used names are provided as well (based on the OpenSSL website from November 1st 15)Most Read Installing SFTP/SSH Server on Windows using OpenSSH
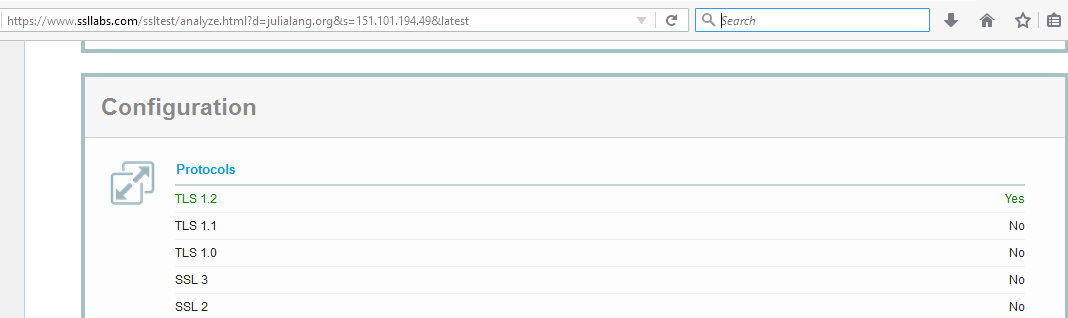



Curl Showing Its Age With Ssl Error Dr John S Tech Talk




Top 10 Ssl Security Vulnerability And Solution Part 2 Sap Blogs
Disabled RCA following KB HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms\PKCS "Enabled"=dword Now vulnerability scanner is showing these as weak ciphers $ /openssl ciphers V 'ALLCOMPLEMENTOFALL' sort grep ' TLSv1 ' 0x00,0xAE PSKAES128CBCSH56 TLSv1 Kx=PSK Au=PSK Enc=AES(128) Mac=SH56 0x00,0xAF PSKAES256CBCSHA384 TLSv1 Kx=PSK Au=PSK Enc=AES(256) Mac=SHA384 0x00,0xB0 PSKNULLSH56 TLSv1 Kx=PSK Au=PSK Enc=None Mac=SH56 0x00,0xB1 PSKNULL We can see every product used its own naming conversions on the ciphers used Ex openssl , Java , Looking at the names they are different but they are same by the nature of algorithm ,key length used etc




Install The Zabbix Agent Enable Tls Psk On Centos And Rhel 19 Cybersecurity Linux Services Across Australia




Psk Authentication Emq Docs
Update associated global variables (only required in ProxySQL v1x releases, not required for ProxySQL v2x) If you want to connect to the same server with both SSL and nonSSL you need to configure the same server in two differentCiphers With curl's options CURLOPT_SSL_CIPHER_LIST and ciphers users can control which ciphers to consider when negotiating TLS connections TLS 13 ciphers are supported since curl 761 for OpenSSL 111 with options CURLOPT_TLS13_CIPHERS and tls13ciphersIf you are using a different SSL backend you can try setting TLS 13 cipher suites by using the respective regular$ openssl ciphers eecdharsaaes128 sed 's// /g' tls_aes_256_gcm_sha384 tls_chacha_poly1305_sha256 tls_aes_128_gcm_sha256 ecdhersaaes128gcmsha256 ecdhersaaes128sha256 ecdhersaaes128sha $ openssl ciphers kecdhepskaes128 sed 's// /g' tls_aes_256_gcm_sha384 tls_chacha_poly1305_sha256 tls_aes_128_gcm_sha256 ecdhepsk
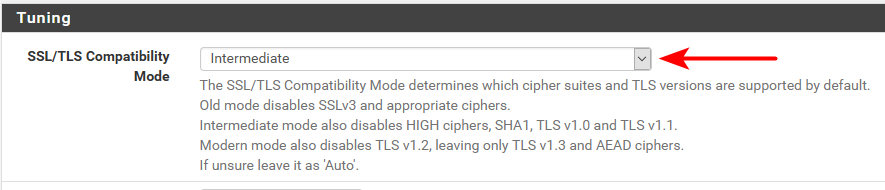



How To Disable Sslv3 With Haproxy Netgate Forum




Elb Insecure Ssl Ciphers Trend Micro
The text was updated successfully, but these errors were encountered #listenersslexternalciphers = ECDHEECDSAAES256GCMSHA384, listenersslexternalpsk_ciphers = PSKAES128CBCSHA,PSKAES256CBCSHA,PSK3DESEDECBCSHA,PSKRC4SHA Then, enable the emqx_psk_file plugin $ emqx_ctl plugins load emqx_psk_file The configuration file for PSK is etc/psktxt A colon is used to separate the PSKEnc=AES(128) Mac=SH56 ECDHEPSKAES128CBCSHA TLSv1 Kx=ECDHEPSK Au=PSK Enc=AES(128) Mac=SHA1 Certificates certificates with RSA keys and SHA1 or SH56 signatures certificates with EC keys and DSA or SH56 signatures;



Support For Tls Psk With Aes 128 Cbc Sha256 Issue 6 Openmobilealliance Oma Lwm2m For Developers Github




Openssl Ciphers Stuff I M Up To
ecdhecdsaaes128sha aes128gcmsha256 aes128sha256 aes128sha seedsha camellia128sha ideacbcsha pskaes128cbcsha ecdhersarc4sha ecdheecdsarc4sha ecdhrsarc4sha ecdhecdsarc4sha rc4sha rc4md5 pskrc4sha ecdhersadescbc3sha ecdheecdsadescbc3sha srpdss3desedecbcsha srprsa3desedecbcsha srpCipher suites The following cipher suites listed below are supported for successfully securing the network connection between Paddle and your endpoint TLS_AES_256_GCM_SHA384 TLS_CHACH0_POLY1305_SH56 TLS_AES_128_GCM_SH56 ECDHEECDSAAES256GCMSHA384 ECDHERSAAES256GCMSHA384 DHERSAAES256GCMSHA384Advertisement Advertisement Contribute Donate $9;




Hp Ilo4 Ssl Circular Reference Help Let S Encrypt Community Support



Cisco Com
$ openssl ciphers v 'PSK' PSKAES256CBCSHA SSLv3 Kx=PSK Au=PSK Enc=AES(256) Mac=SHA1 PSKAES128CBCSHA SSLv3 Kx=PSK Au=PSK Enc=AES(128) Mac=SHA1 PSKRC4SHA SSLv3 Kx=PSK Au=PSK Enc=RC4(128) Mac=SHA1 PSK3DESEDECBCSHA SSLv3 Kx=PSK Au=PSK Enc=3DES(168) Mac=SHA1 How I can get following cipherSecure hash algorithms SHA1, SH24, SH56, SHA384, SHA512 for computing a condensed representation of electronic data (message) When a message of any length less than 2 64 bits (for SHA1, SH24, and SH56) or less than 2 128 (for SHA384 and SHA512) is input to a hash algorithm, the result is an output called a message digestUser Approved Software Total Downloads 167,216,108 Rating 48 out of 175 reviews SourceForge Review Recommend Tweet;
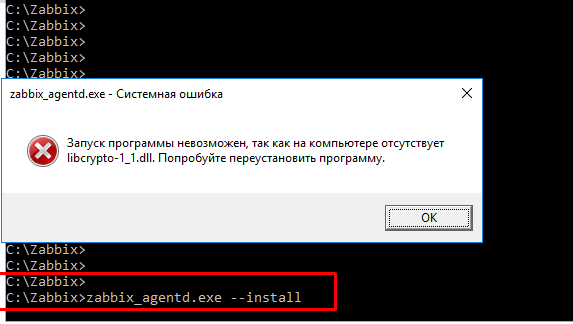



Zbxnext 3047 Windows Zabbix Agent Binary Is Not Compiled With Tls Support Zabbix Support




Zabbix4 X How Secure Data Secure Data Programmer All
nginx with GmSSL Contribute to pengtianabc/nginxgm development by creating an account on GitHubSecure DHEPSKAES256CCM8 Secure DHERSAAES128CCM8 Recommended ECDHEECDSAAES256GCMSHA384 Weak DHEPSKAES256CBCSHA384 Weak ECDHEECDSAAES256SHA384 Insecure ADHAES128SH56 Weak ECDHEPSKAES128CBCSHA Secure DHEPSKAES128CCM Insecure RSAPSKNULLSHA384Supported TLS Version ¶ TLSv1 (If enabled) TLSv11 (If enabled) TLSv12;



Tls Psk Issue 451 Eclipse Paho Mqtt Python Github




Extreme Access Control Eac Freeradius Default Cipher List Extremecloud Iq Site Engine Extreme Management Center




Seven Grades Of Perfect Forward Secrecy




Trb141 Vpn Teltonika Networks Wiki



Github Bmdan Ssl Protocol Checker Quickly Determine Which Protocols And Cipher Suites Are Supported By A Destination Server




Pdf End To End Iot Security Middleware For Cloud Fog Communication




Pdf Guidelines For The Selection Configuration And Use Of Transport Layer Security Tls Implementations Semantic Scholar
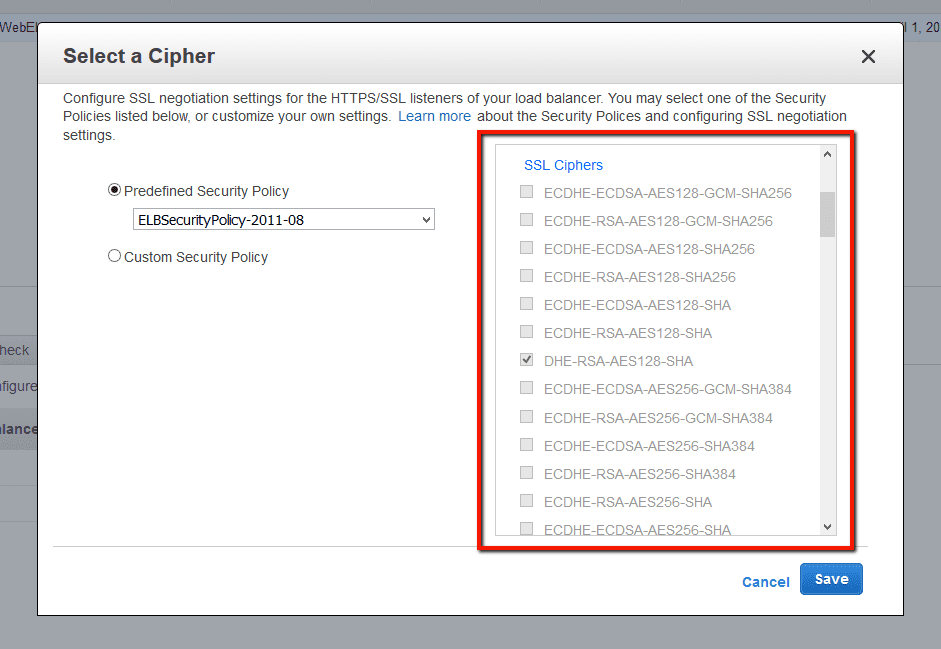



Elb Insecure Ssl Ciphers Trend Micro



Support Avaya Com




6 Openssl Command Options That Every Sysadmin Should Know Enable Sysadmin




Openldap Tls Cipher Options R Linuxadmin




Is The Order Of Cipher Names In Tidserveriohandlersslopenssl Ssloptions Cipherlist Important Stack Overflow




Ken Felix Security Blog Pfs And Web Clients Browsers Supports




Out Of Sight Out Of Mind With Security That S Out Of Your Mind
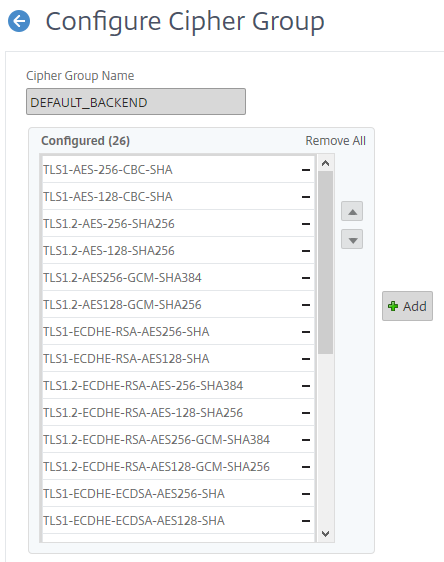



Netscaler Ssl Ciphers Fun With Bitwarden It Randomness



Link Springer Com



Ftp1 Digi Com
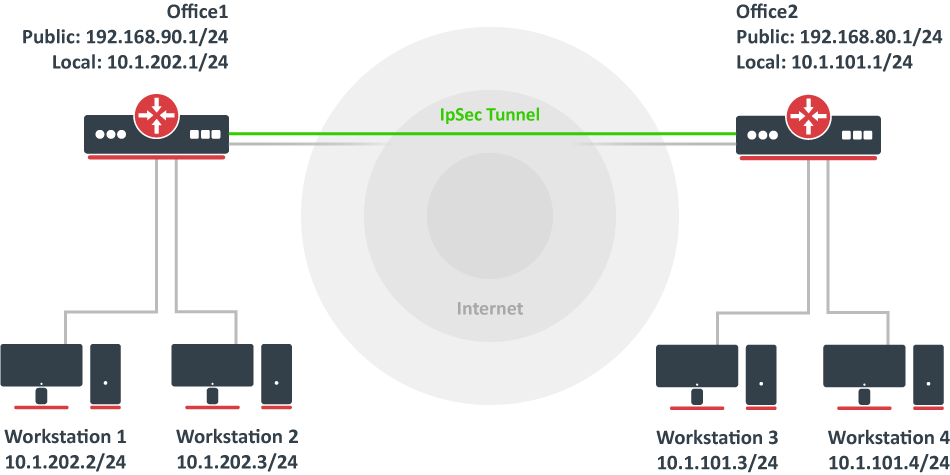



Ipsec Routeros Mikrotik Documentation



4d Plugin Common Crypto Tls1 H At Master Miyako 4d Plugin Common Crypto Github




Mikrotik Site To Site Ipsec When One Router Has A Dynamic Wan Ip Address Mivilisnet



Cipher Suite Practices And Pitfalls Devcentral
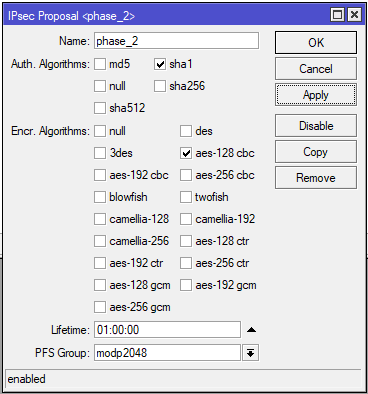



Mikrotik Od Zera Vpn Site To Site Ipsec Ikev2 Psk 09 Just Another It Guy




Emq X Authentication 2 Core Concepts And Configuration Points Of Mqtt Connection Authentication Emq



Comparison Between Ipsec And Proposed Suit Protocols 59 Download Scientific Diagram
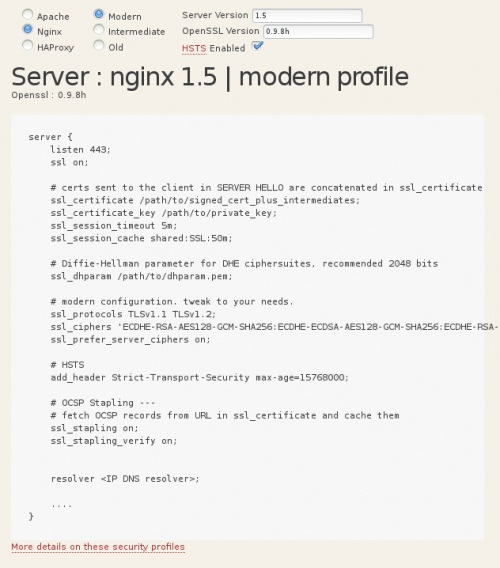



Nginx Security Server Side Tls Larry的博客 Csdn博客
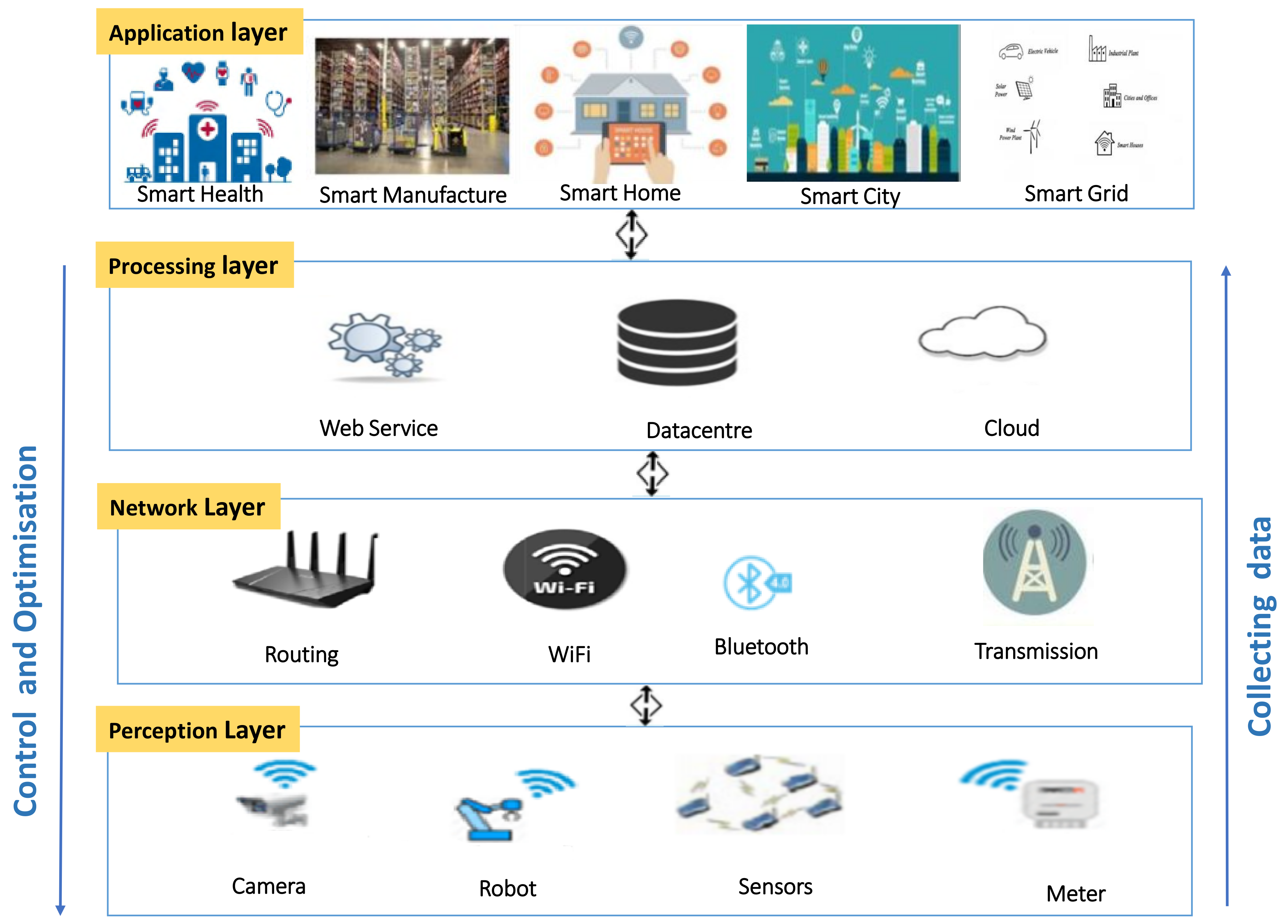



Sensors Free Full Text Internet Of Things For System Integrity A Comprehensive Survey On Security Attacks And Countermeasures For Industrial Applications Html



Cipher Suite Practices And Pitfalls Devcentral




How To Check Supported Tls And Ssl Ciphers Version On Linux 2daygeek




Apache Ssl Cipher Suites Perfect Forward Secrecy Weberblog Net



Server User Guide Atomjump Messaging




Wallix Bountysource
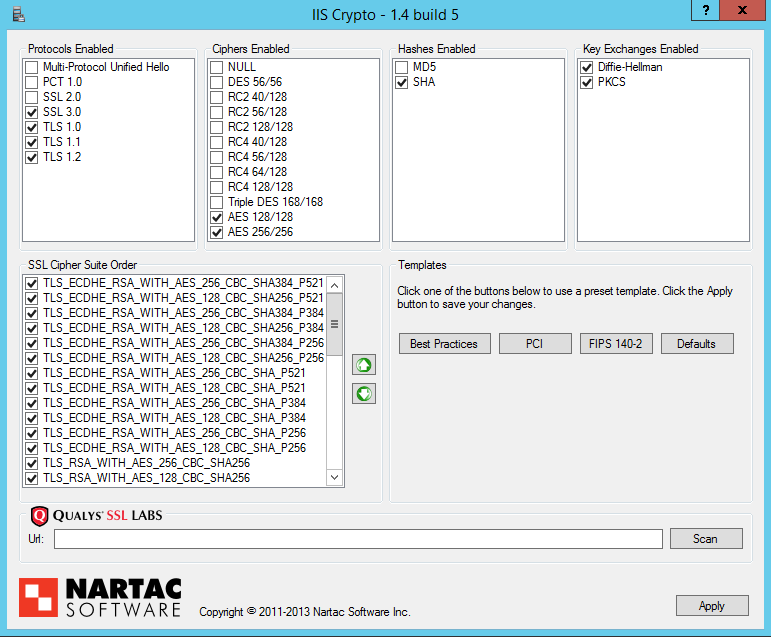



Applied Crypto Hardening Bettercrypto Org



Unsupported Cipher Suite Ecdhe Ecdsa Aes128 Sha256 Ecdhe Ecdsa Aes128 Sha256 Issue 9775 Netty Netty Github




Ssl Yuri S Technology Blog




Elb Insecure Ssl Ciphers Trend Micro
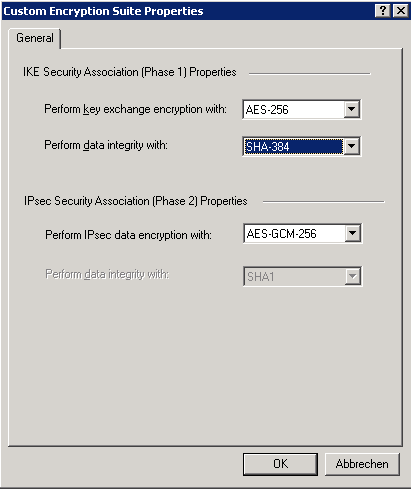



Applied Crypto Hardening Bettercrypto Org



Ipa Go Jp




Ssl Ciphers Internet Lab Ru
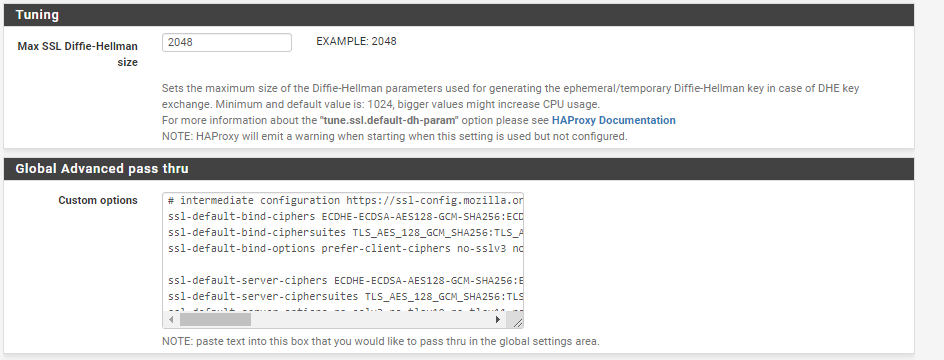



How To Disable Sslv3 With Haproxy Netgate Forum



Unix Command Openssl Ciphers Unixshadow




Krb1 Tunnel Acceleration For Wireless Access Points Google Patents




Psk Authentication Emq Docs




Psk Authentication Emq Docs




Top 10 Ssl Security Vulnerability And Solution Part 2 Sap Blogs



Cipher Suite Practices And Pitfalls Devcentral




Hp Ilo4 Ssl Circular Reference Help Let S Encrypt Community Support
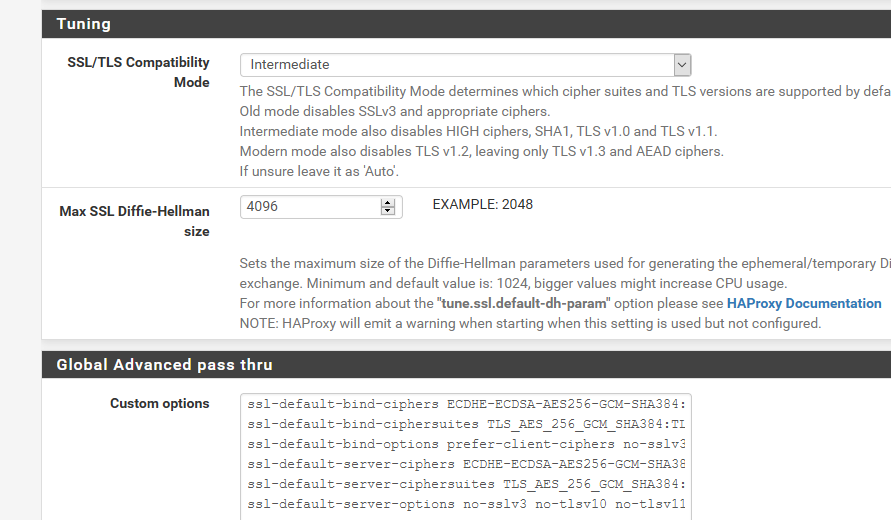



How To Disable Sslv3 With Haproxy Netgate Forum




How To Check Supported Tls And Ssl Ciphers Version On Linux 2daygeek



Pjm Com




Linux Octopus Tentacle Not Installing Octopus Server Octopus Deploy



Campus Barracuda Com




Openssl Configuration File Download Scientific Diagram
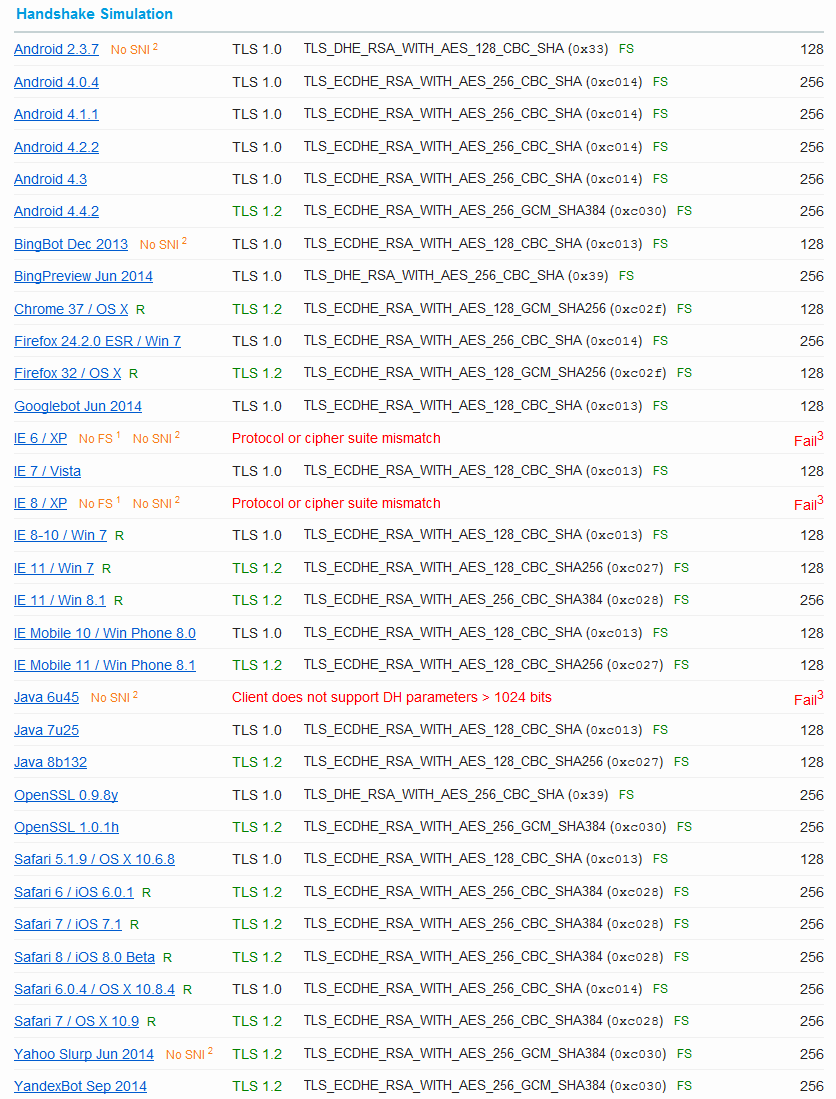



Apache Ssl Cipher Suites Perfect Forward Secrecy Weberblog Net
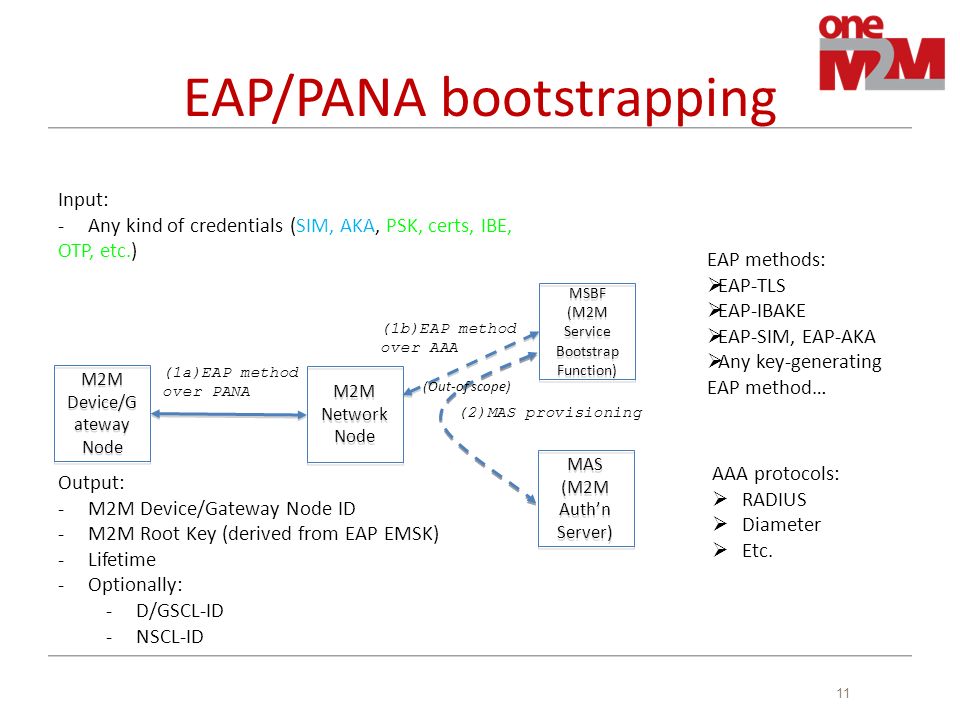



Presentation Of Etsi Tc M2m Security Features Group Name Wg4 Securtity Source Francois Ennesser Gemalto Meeting Date Agenda Item Sec Ppt Download
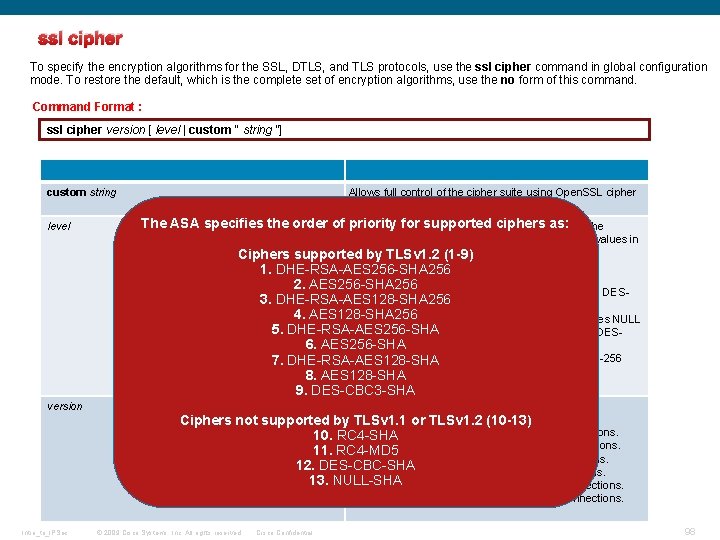



Ssl Tls And Dtls Introtoipsec 09 Cisco Systems
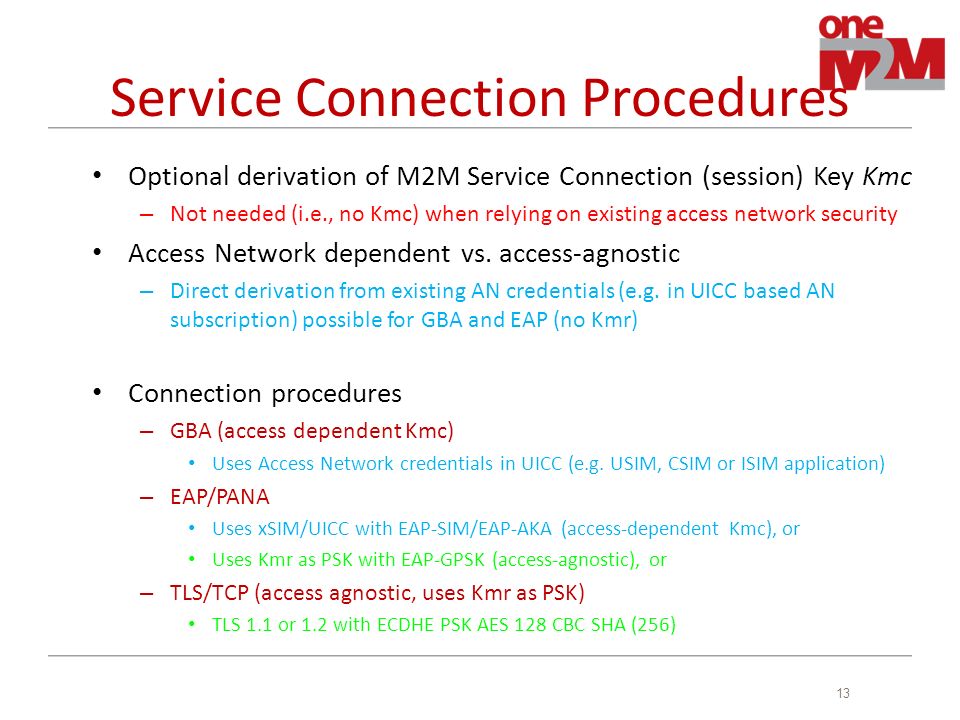



Presentation Of Etsi Tc M2m Security Features Group Name Wg4 Securtity Source Francois Ennesser Gemalto Meeting Date Agenda Item Sec Ppt Download
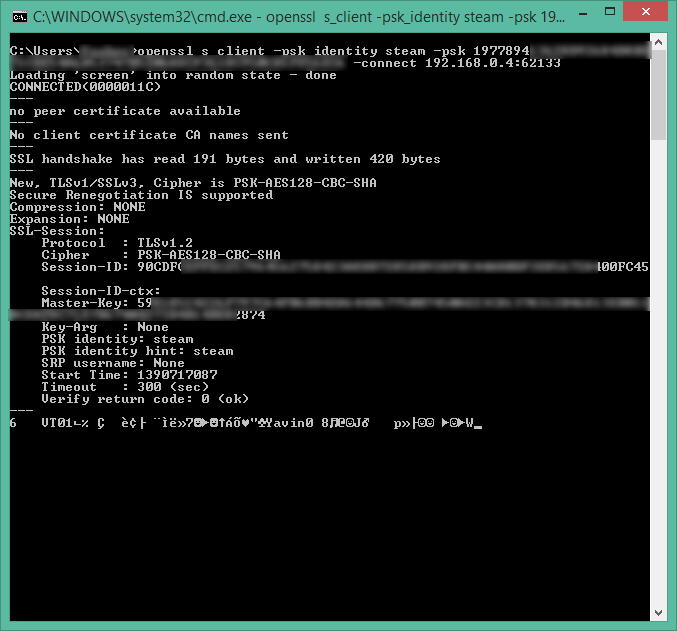



Decoded Steam In Home Streaming Control Protocol Coding Range




Trb141 Vpn Teltonika Networks Wiki
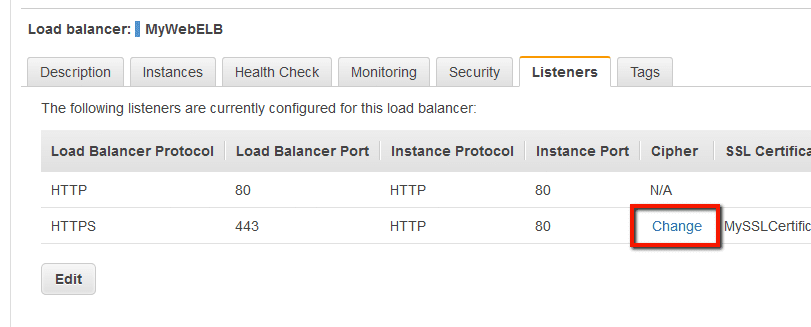



Elb Insecure Ssl Ciphers Trend Micro
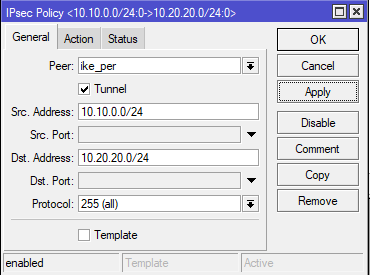



Mikrotik Od Zera Vpn Site To Site Ipsec Ikev2 Psk 09 Just Another It Guy




C Wrapper Api Guide December 7th 15 Version Pdf Free Download




The Certificate Generated With Certbot Does Not Work On Windows Xp Help Let S Encrypt Community Support




Strong Ssl Security On Apache2 Raymii Org
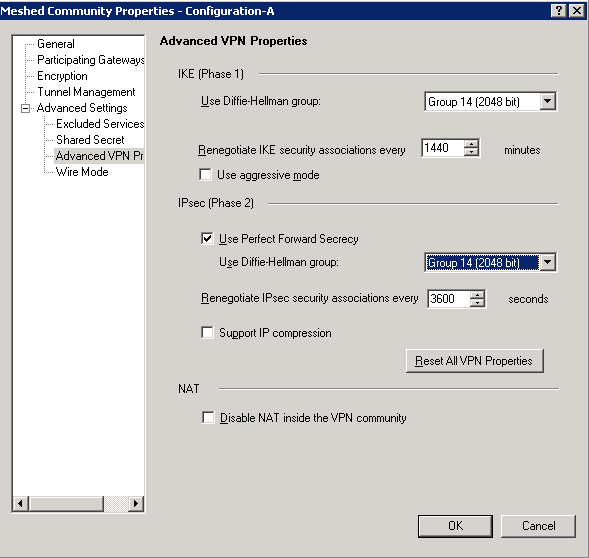



Applied Crypto Hardening Bettercrypto Org



Why Is My Server Still Rated With T I Want B



Support Industry Siemens Com



St Security Authentication And Encryption With Ssl Tls



Openssl Dr John S Tech Talk



Spinifexdragon Com



Support Industry Siemens Com
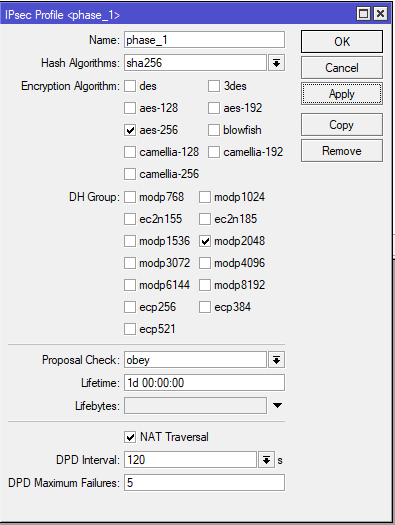



Mikrotik Od Zera Vpn Site To Site Ipsec Ikev2 Psk 09 Just Another It Guy
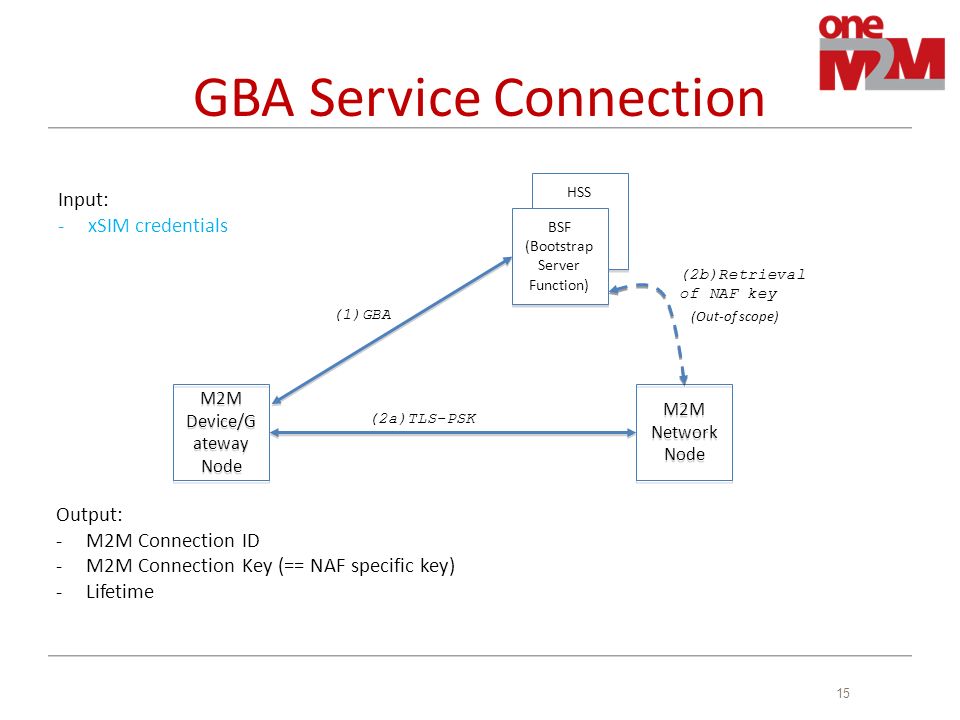



Presentation Of Etsi Tc M2m Security Features Group Name Wg4 Securtity Source Francois Ennesser Gemalto Meeting Date Agenda Item Sec Ppt Download




Emq X Authentication 2 Core Concepts And Configuration Points Of Mqtt Connection Authentication Emq



Forward Into The Ssl Mist Afk Geek Blog




Install The Zabbix Agent Enable Tls Psk On Centos And Rhel 19 Cybersecurity Linux Services Across Australia



Dd Wrt Forum View Topic New Beta R 09 13 19 R



0 件のコメント:
コメントを投稿